BLOC: A Blockchain-Oriented Context AI Protocol for
Decentralized Crypto Operations
01/ Abstract
BLOC is a decentralized framework for discovering and executing cryptocurrency operations autonomously. It introduces Bloc Assistants, which integrate contextual data from on-chain and off-chain sources to identify opportunities and execute actions without central control. The design emphasizes a modular, function-driven architecture: separate modules handle token discovery, smart execution routing across exchanges, and strategy recommendations with persistent context memory. Strong cryptographic primitives (digital signatures, multi-signature schemes, hashing) and a robust permission model ensure that transactions are securely authorized and data access is controlled. This paper outlines the purpose and philosophy of BLOC, details its protocol-level operation with pseudocode, and demonstrates how systemic incentives align participants to maintain a reliable, trust-minimized network.
02/ Introduction
Cryptocurrency markets operate at high speed across disparate platforms. Currently, discovering promising tokens (e.g. new assets or trends) and acting on that information requires manual research on social media or block explorers, followed by manual trades on exchanges. This process is fragmented and often centralized through third-party services or custodial trading bots. Bloc Protocol eliminates these inefficiencies by providing a peer-to-peer, automated assistant that can both discover information and execute transactions in a trustless manner.
Bloc Protocol defines an open standard for Blockchain-Oriented Context (BLOC) management. A Bloc Assistant following this protocol can gather signals from public data, formulate a strategy, and carry out crypto operations – all while the user retains cryptographic control over funds. The system requires no trusted middleman: it leverages the blockchain for transaction execution and uses verifiable data sources. By design, it is timeless and abstract, focusing on fundamental incentives and behaviors rather than any single platform. In the following sections, we describe BLOC’s philosophy, architecture (discovery, execution, strategy modules), security model, and the incentives that make the network sustainable.
03/ Design Philosophy
Bloc Protocol’s design is guided by principles analogous to those behind early cryptocurrency systems:
- Decentralization: Every Bloc Assistant operates without a central server or authority. Control is distributed to users; each user can run their own assistant or choose from a network of community-run assistants, ensuring no single point of failure.
- Modularity: The protocol is function-call driven and modular. Discovery, execution, and strategy logic are separated into interchangeable modules. This allows updates or customization of one component without affecting the others, fostering an open ecosystem of module implementations.
- Minimal Trust Assumptions: Users maintain control over private keys and approvals. The assistant cannot spend funds without user authorization. All interactions are either on-chain (enforced by blockchain consensus) or cryptographically verified off-chain, removing the need to trust the assistant’s intentions.
- Context Awareness: Unlike stateless scripts, a Bloc Assistant retains context from past operations. By remembering prior events and user preferences, it can make informed decisions that persist over time, improving efficiency and avoiding repetitive or conflicting actions
- Incentive Alignment: The protocol is structured so that participants benefit by behaving honestly. An assistant that provides profitable strategies and executes efficiently will be sought out by users (or beneficial to its owner), while malicious or inefficient behavior is discouraged by cryptographic checks and economic consequences (e.g. wasted fees or loss of reputation).
These principles ensure that BLOC remains focused on protocol behavior and incentives rather than relying on any centralized service or short-lived market trend.
04/ System Overview: Decentralized Discovery and Execution
Bloc Protocol marries information discovery with transaction execution in a unified, decentralized system. At its core is the concept of a Bloc Assistant, a program that orchestrates three key functions on behalf of a user:
1. Token Discovery: Scanning a variety of sources – from on-chain blockchain data to off-chain social feeds – to identify tokens or opportunities of interest in a permissionless way.
2. Strategy Formulation: Analyzing the gathered context and the user’s current state (portfolio and preferences) to recommend or decide on an action (e.g. buy, sell, hold, or observe).
3. Execution Routing: Carrying out the chosen operation by interacting with cryptocurrency exchanges, either decentralized (DEX) or centralized (CEX), in a manner that optimizes performance (minimizing slippage, fees, and latency).
Crucially, BLOC includes a native token (BLOC) that serves as the protocol’s unit of account and utility. While this paper avoids any specific tokenomics, the BLOC token can be used to facilitate operations (for example, as gas fees for using certain modules or as a staking bond to ensure honest behavior). The protocol itself is blockchain-agnostic: it can function across multiple chains and platforms as long as the assistant has access to those networks and data sources. All components communicate through defined function-call interfaces, enabling a standard language for discovery and trade execution requests.
A typical Bloc Assistant workflow proceeds as follows:
- It initiates a discovery cycle to gather fresh data on tokens and market conditions.
- Based on the new data and its stored context, it decides on a strategy (e.g. detecting a trending token that fits the user’s criteria for investment).
- If an action is warranted, the assistant prepares a transaction for execution (such as a trade transaction).
- The user’s permissions are checked or requested (the assistant may request a signature if needed) before broadcasting the transaction to the relevant exchange or blockchain.
- After execution, the outcome and any new context (price paid, new holdings, etc.) are fed back into the assistant’s memory for use in future decisions.
This entire process is done autonomously by the assistant under the hood, but the user can always audit or intervene. The discovery and strategy steps happen off-chain (to analyze data), whereas the execution step results in an on-chain transaction (or a secure API call to an exchange). By combining these steps, Bloc Protocol enables decentralized discovery and execution – the assistant can proactively find opportunities and act, reducing reliance on centralized platforms that might offer only static data or only execution without intelligence.
05/ Architecture
The BLOC architecture is implemented as a collection of modular components that interact through explicit function calls. The Bloc Assistant is essentially an orchestrator that invokes these modules in sequence. Each module focuses on a specific task, and together they create a pipeline from information to action. Pseudocode is provided to illustrate the internal logic of each part of the protocol.
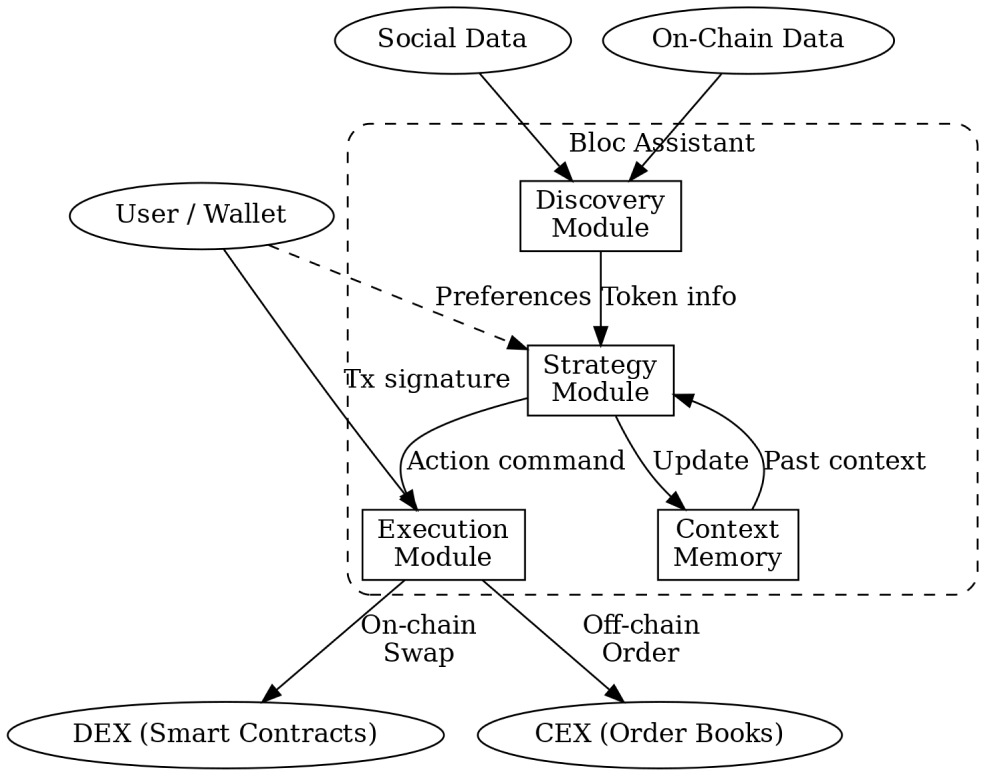
Figure 1: High-level Bloc Assistant architecture (dashed box) with dedicated Discovery, Strategy, Execution, and Context Memory modules. External data sources (social feeds and on-chain events) feed into the Discovery Module. The Strategy Module combines new token information with historical context and user preferences to decide on actions. The Execution Module interfaces with decentralized (smart contracts) or centralized (order books) exchanges to carry out trades, while the user’s wallet provides cryptographic approval (e.g. signatures) for any transaction, ensuring the user remains in control.
At a high level, the assistant’s operation can be represented by a simple loop:

This illustrates how the modules fit together: the Discovery Module produces input for the Strategy Module, which decides to invoke the Execution Module, and then state is recorded. We now examine each module in detail.
06/ Token Discovery Module
The Discovery Module is responsible for gathering and filtering signals about tokens or market events. It monitors two broad classes of sources:
- On-Chain Sources: Blockchain data such as newly deployed contracts, transaction volume spikes, significant token transfers, or changes in decentralized exchange liquidity. These provide objective, verifiable indicators of activity.
- Off-Chain Social Sources: Information from social platforms, forums, or news (for example, trending mentions of a token on a decentralized social network or developer announcements). These provide contextual hints about market sentiment and emerging trends.
The module operates by aggregating these feeds and extracting tokens or assets of interest. In practice, this could involve querying APIs or running nodes that watch blockchain events. The logic ensures that the process is trust-minimized: whenever possible, data is cross-verified (for instance, if a social source claims a token is popular, the assistant might verify that the token’s smart contract exists on-chain and is active).
Simplified pseudocode for discovery:

Here, combine_and_rank merges the two sets of findings, perhaps giving higher rank to tokens that appear in both categories (indicating both hype and on-chain activity). The output is a list of token symbols or addresses and possibly a heuristic score for relevance. This list is passed to the Strategy module.
Because the Discovery module can incorporate arbitrary data sources, it is extensible. For example, one implementation might include open-source code repository activity (to find active project tokens), while another might focus on governance forums. The BLOC protocol defines standard function calls for discovery results, so any such extension still produces a list of token opportunities to the next stage. The key is that discovery is continuous and autonomous: an assistant keeps listening for new information in real-time, akin to how a node in a cryptocurrency network listens for transactions.
07/ Execution Routing Module
The Execution Module takes a desired action (typically a trade instruction like “buy X amount of Token Y” or “sell Z of Asset W”) and executes it in the optimal way across available trading venues. It effectively acts as a smart router between decentralized exchanges and centralized exchanges:
- On decentralized exchanges (DEXs), the assistant interacts directly with smart contracts (such as an automated market maker). This involves constructing a transaction to swap tokens on-chain.
- On centralized exchanges (CEXs), the assistant uses secure API calls (if the user has an account there) to place orders on the order book.
The module must decide where and how to execute to maximize the user’s benefit. Important factors include price, liquidity, and slippage. Slippage is the price impact of executing a trade; a core goal is to minimize it. For instance, if a token has shallow liquidity on a DEX, a large buy order will move the price significantly.
The Execution Module would detect this and could either:
- Split the trade across multiple DEXs to draw from several liquidity pools.
- Route the trade (or part of it) to a CEX where an order book might absorb it with less price movement.
This behavior mirrors that of DEX aggregators which split and reroute trades across various DEXes to achieve the best swap rates given the network conditions. The module can compute an optimal execution plan. For example, it may solve an optimization problem to distribute a purchase of 100 tokens across three DEX pools and a CEX such that no single venue incurs excessive slippage. If $R_x$ and $R_y$ are the reserve sizes of a DEX liquidity pool (for tokens X and Y respectively), and a trade of size $\Delta x$ is made, the price impact can be estimated by the constant-product formula:
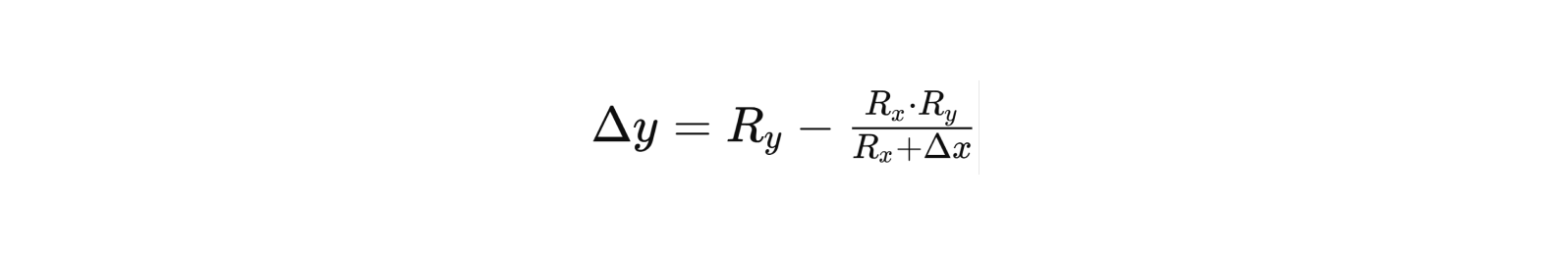
indicating that larger $\Delta x$ relative to $R_x$ yields a larger $\Delta y$ (output from the pool), but with diminishing returns (increasing slippage). The Execution Module aims to keep each $\Delta x$ small relative to $R_x$ by splitting orders, thus reducing slippage.
A pseudocode of the Execution Module’s logic:
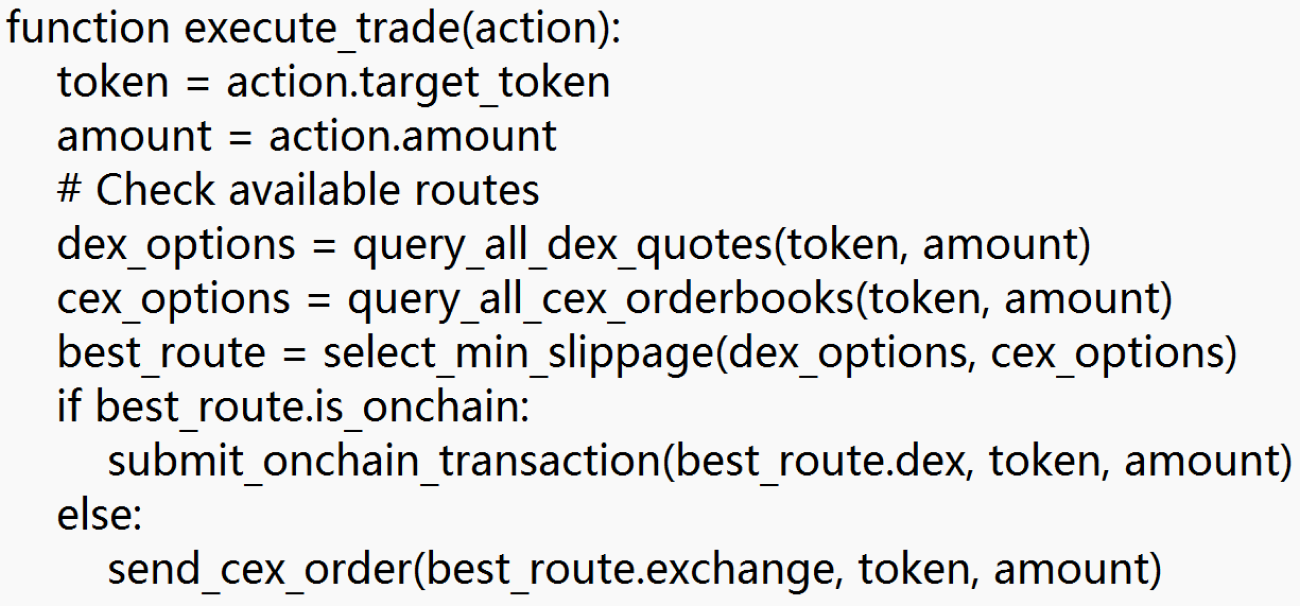
Here, query_all_dex_quotes returns quotes or slippage estimates from multiple decentralized exchanges, and similarly for query_all_cex_orderbooks. The assistant then chooses the route with the best price and acceptable slippage. If the best route involves an on-chain trade, the assistant constructs and submits the transaction to the blockchain (which the user must authorize as described in the Cryptographic Primitives and Permission Model section). If it involves a centralized exchange, the assistant uses the API (with the user’s pre-provided API key permission) to execute.
The Execution Module also performs safety checks. Before executing, it can enforce limits (e.g. not buying above a certain price, or not spending more than a specified amount of the user’s funds), based on user-defined constraints. This prevents unwanted surprises due to rapid market changes. After execution, the module reports the outcome (filled amount, final price) back to the Strategy Module or context memory.
08/ Strategy Module and Context Memory
The Strategy Module is the decision-making brain of the Bloc Assistant. It receives the list of candidate tokens or signals from the Discovery Module and must decide what to do with that information. Its output could be:
- A concrete trading action (e.g., “Buy 10 $TOKEN” or “Sell 0.5 ETH for BTC”), or
- A recommendation presented to the user (if the assistant is in a suggest-only mode), or
- No action, if the best strategy is to hold or wait for more data.
To make these decisions, the Strategy Module leverages Context Memory – a store of historical data and state. Context Memory might include:
- Records of past discoveries and actions (e.g., “Token X was bought last week at price P”).
- The user’s current portfolio and asset allocation.
- The outcomes of previous strategies (profit/loss, missed opportunities, etc.).
- Aggregate market context (e.g., overall market trend or volatility levels observed).
Having this memory allows the assistant to avoid repetitive cycles (for example, not recommending to buy the same token every hour if it’s already held) and to adjust strategies based on what has or hasn’t worked in the past. This design echoes how human decision-makers use memory: the assistant “remembers” and therefore can exhibit consistency and learning over time, rather than treating each cycle as a blank slate.
The Strategy Module can implement any number of trading or investment strategies. One simple approach could be momentum-based: buy tokens that show rising momentum and sell tokens that show declining momentum. For instance, the module could compute a trend indicator for each candidate token using price data:
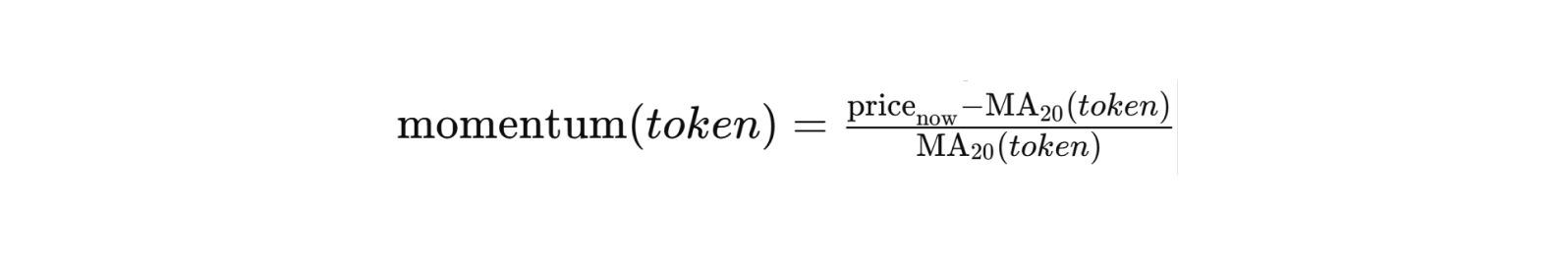
Where $\text MA_20$ is a 20-period moving average price. A positive momentum indicates the price is above the recent average (an uptrend), which might trigger a buy, whereas a negative value indicates a downtrend (perhaps a signal to avoid or sell). More sophisticated strategies could incorporate social sentiment metrics, mean-reversion logic, or portfolio rebalancing rules.
Pseudocode for a basic strategy might look like:
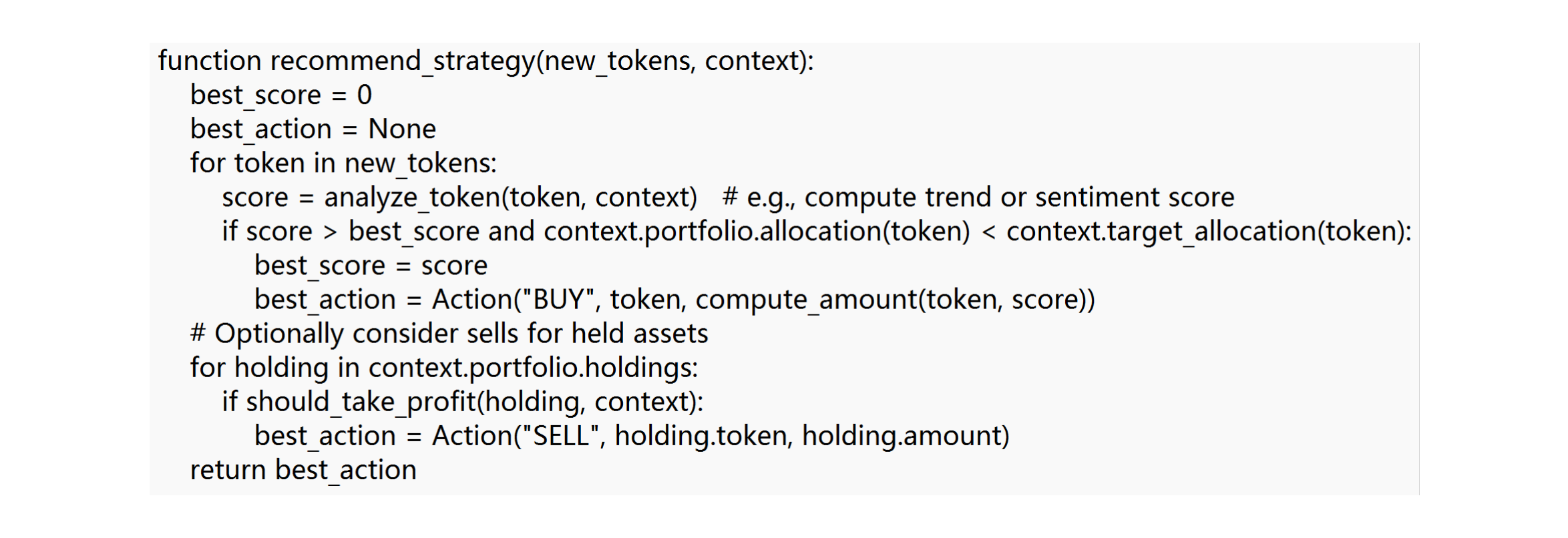
In this outline, analyze_token might combine current data with past context (perhaps the token’s last seen price or whether it was recently traded). The strategy ensures, for example, that it doesn’t exceed some target allocation for any token. It also considers an opposite action: if the context indicates a held asset has hit a profit target or risk limit, it prepares a sell action. The result best_action could be None if no compelling move is found, meaning the assistant will simply wait.
The Strategy Module’s output (if any) is then passed to the Execution Module as described. If the assistant is fully autonomous and pre-authorized, it might trigger execution immediately. Alternatively, the assistant could operate in a “human-in-the-loop” mode where it presents the strategy to the user for confirmation (for example, via a notification: “Assistant recommends buying 10 of TokenX at $5 each”). In either case, after a decision and any execution, the assistant updates the Context Memory:
- If a trade was executed, record the details (token, amount, price, time).
- Update the current portfolio state in memory.
- Possibly adjust any strategy parameters based on outcome (this could be considered a learning aspect, though the protocol does not mandate a specific learning algorithm).
By maintaining this cycle of observe (Discovery) → decide (Strategy) → act (Execution) → learn (Memory), Bloc Assistants implement a closed-loop system for automated crypto operations. The protocol-level details ensure each step is transparent and auditable, and the user can inject preferences at any stage (for example, what sources to trust, which strategies to employ, and what risk limits to enforce).
09/ Cryptographic Primitives and Permission Model
Security is paramount in Bloc Protocol. All critical actions require cryptographic confirmation to ensure that the assistant cannot misappropriate funds or falsify data. The protocol employs the following cryptographic primitives and mechanisms:
- Digital Signatures for Transactions: Any blockchain transaction (such as a token swap or transfer) initiated by the Execution Module must be signed by the user’s private key (or an authorized key) before it becomes valid. This leverages standard public-key cryptography – for example, ECDSA or EdDSA signatures – to authenticate the origin of transactions. Only someone with the correct private key can produce a valid signature, so unauthorized parties (including a compromised assistant) cannot forge transactions. With 256-bit elliptic curve keys, the security level is approximately $2^128$ operations to break, which is computationally infeasible. This ensures that fund transfers are effectively under the user’s sole control.
- Multi-Signature and Delegated Control: In scenarios where partial automation is desired, BLOC supports multi-signature (multisig) schemes. A multisig wallet requires a predefined quorum of signatures to approve a transaction. For example, a wallet could be configured such that both the user and the Bloc Assistant’s keys must sign any trade (2-of-2 multisig), or a 2-of-3 scheme could include a backup key. Multi-signature arrangements prevent unilateral action: the assistant alone cannot move funds, and the user alone might not execute complex strategies without the assistant. An extension of this idea is delegated keys: the user can delegate limited authority to the assistant via a smart contract wallet. In practice, this might mean the user’s main cold wallet holds the funds but grants a “trading key” limited powers (e.g. can trade certain whitelisted tokens, but not withdraw to arbitrary addresses). Such a dual-key setup greatly reduces risk, as even if the assistant’s hot key is compromised, the attacker cannot steal funds — they could only perform trades in a restricted manner, which the user could later reverse or halt. The permission model of BLOC allows for these flexible setups, depending on how much autonomy the user wants to grant their assistant.
- Encrypted Communications and Data: When Bloc Assistants fetch data from external sources or communicate with exchange APIs, those channels are encrypted (e.g., using HTTPS/TLS or end-to-end encryption for decentralized feeds). This prevents adversaries from tampering with or eavesdropping on the data that the assistant uses to make decisions. Moreover, the protocol encourages verifying data authenticity as well. For example, if a data feed provides a cryptographic proof (like an oracle’s signed message or a Merkle proof that a certain on-chain event occurred), the assistant will validate that proof before trusting the data. This ties into the idea that whenever possible, the assistant favors verifiable data over merely trusted data.
- Hashing and Integrity: The assistant can hash critical records (like a history of actions or state snapshots) and optionally store those hashes on a blockchain to create an immutable audit trail. Although not strictly required, such a feature adds accountability: the user (or anyone) can later verify that the assistant’s reported actions match what was committed to the ledger. If context memory is stored off-chain (e.g. locally or in decentralized storage), hashing it periodically and anchoring it on-chain ensures it hasn’t been tampered with undetected. This is analogous to creating checkpoints that can be independently verified.
- Access Control for APIs: If a Bloc Assistant needs access to a centralized exchange or any user account, it uses API keys or OAuth tokens provided by the user. The protocol insists that these credentials have restricted scope. For instance, an exchange API key might be set to trading-only (no withdrawals) and possibly with a rate limit or spending cap. This way, even if an assistant is exploited, the damage is limited. Additionally, the assistant itself never exposes these keys; they remain encrypted in storage and are only used within the secure execution of the module that needs them.
- Through these measures, the Bloc Protocol creates a permission model where the user’s consent is cryptographically required at every important step. The user retains custody of assets at all times – the assistant cannot unilaterally transfer funds to itself or anywhere else not approved. Data access is similarly controlled; the assistant cannot exfiltrate private user data or keys because it’s never given more permission than necessary. From a cryptographic perspective, Bloc Assistants are self-contained and will sign only what they are allowed to, and nothing more.
- By using well-tested primitives (secure hash functions, digital signatures, encryption) and aligning with existing standards (like multisig wallets and smart-contract-based accounts), BLOC ensures security without reinventing the wheel. It focuses on combining these primitives in a novel context (automated, contextual operation) while keeping the trust model as simple as possible. In essence, “don’t trust, verify” is applied at each layer of the assistant’s operation.
10/ Incentives and System Behavior
For any decentralized protocol, designing proper incentives is key to long-term viability. Bloc Protocol’s incentive structure aligns the interests of users, assistants, and any third-party contributors (like module developers or data providers) with the health of the system:
- User Incentives: Users adopt Bloc Assistants to improve outcomes (catch opportunities early, execute trades faster and at better prices) and to save time. Because the assistant operates under the user’s control, the user does not sacrifice security for this convenience. The costs to the user are limited to transaction fees and possibly a service fee to an assistant operator (or a small amount of BLOC tokens to access certain advanced modules), but these are worthwhile if the assistant’s performance adds value. Users can also switch assistants or run their own, which means assistants must remain competitive in strategy performance and fee cost to attract users. This open market pressure incentivizes continuous improvement of strategies in a decentralized way.
- Assistant Operator Incentives: If Bloc Assistants are offered as a service by skilled developers or community members, those operators could earn BLOC tokens or fees from users who utilize their assistant instances or modules. However, to earn this, their assistants need a proven track record (since users can verify past performance on-chain). This creates an incentive for operators to use sound strategies and maintain secure, reliable infrastructure. Importantly, any operator who behaves maliciously or incompetently will quickly lose users: for example, an assistant that frequently recommends bad trades will be abandoned. An operator who tries to misbehave (say, by front-running a user’s trades for personal gain) will be hampered by the protocol’s cryptographic restrictions and can be identified via the audit trail. In essence, honest, effective behavior is rewarded with continued usage and reputation, while dishonesty is self-punishing.
- Module Developers and Data Providers: Because of the modular architecture, specialists might develop improved Discovery modules (perhaps one that has superior algorithms for parsing social data, or a faster Execution module integrating a new DEX). They can publish these modules under the open protocol. Users or assistant operators can then opt to incorporate those modules. Developers could be rewarded by usage fees or through token incentives – for instance, a popular module might charge a tiny fee in BLOC for each use, or module developers might be incentivized by holding BLOC tokens that gain value as the protocol’s usage grows. The open-standard approach means innovation is not limited to a single team; anyone can improve a part of the system. This fosters a competitive yet collaborative environment similar to how miners or validators in a blockchain compete yet together strengthen the network.
- Network Effects: All Bloc Assistants benefit from the growth of the network. If many assistants are running, collectively they are observing a vast array of data and market events. While they might not directly share proprietary information, the very act of multiple agents acting on inefficiencies will drive markets to be more efficient. For example, if one assistant finds an arbitrage and executes it, that opportunity vanishes for others – but it also means the overall market pricing becomes more accurate. In a sense, Bloc Assistants as a whole help enforce the idea of “no free lunch” in markets – if any pricing discrepancy or trend emerges, at least one assistant will likely act on it, which quickly levels the playing field. This dynamic is analogous to miners in Bitcoin: each is self-interested, but their collective action secures the network. Here, each assistant pursuing profit also contributes to a more informationally efficient market. Systemically, this reduces the advantage of any insider or centralized entity, reinforcing decentralization and fair access.
- BLOC Token Utility: The BLOC token can be used to further align incentives. For instance, assistant operators might stake a certain amount of BLOC as collateral. If an assistant violates protocol rules or behaves maliciously (for example, attempting an unauthorized transaction which would be caught by the permission system), a portion of this stake could be slashed, penalizing bad behavior. Conversely, an assistant that successfully completes many operations could earn rewards or reputation benefits tied to their stake. This is analogous to how proof-of-stake blockchains incentivize validators to be honest by bonding capital. While details of a staking or reward mechanism are beyond the scope of this paper, the principle is that the token economically reinforces good behavior and deters abuse. At the same time, the token’s role in module marketplaces (paying for data feeds or premium strategies) creates a self-sustaining ecosystem: those who contribute value to the system are compensated in a currency that represents the system’s value.
The Bloc Protocol is designed so that each participant, by trying to maximize their own benefit, also maintains or enhances the network’s integrity and utility. Users get better results with minimal trust, good assistants gain usage (and potentially fees), and the overall market moves toward greater decentralization and transparency. This balance of incentives echoes the approach of Bitcoin’s design, where miners secure the network for rewards – analogously, here assistants improve market access and efficiency and are rewarded by the opportunities they capitalize on.
11/ Conclusion
We have presented Bloc Protocol (BLOC), a minimalist yet powerful framework for decentralized discovery and execution of crypto-related operations. The protocol is built on the idea of Bloc Assistants that can autonomously bridge the gap between information and action in the cryptocurrency domain while preserving user control and security. By compartmentalizing the workflow into discovery, strategy, and execution modules, the system remains flexible and upgradeable. The inclusion of context memory ensures that these assistants operate with a sense of history and continuity, an abstract concept that greatly enhances decision-making – akin to an experienced human trader, but enforced through code.
In true Nakamoto fashion, BLOC leverages incentives and cryptography instead of trust. All critical actions are secured by cryptographic signatures and optional multi-signature schemes, ensuring that no assistant can bypass user intent. The economic design incentivizes honest behavior and continual improvement of the ecosystem’s components without needing a central coordinator.
Bloc Protocol focuses on protocol behavior and long-term viability rather than short-term market trends or promotional promises. It does not rely on any proprietary technology or centralized data feeds – only on open networks and algorithms. This makes the design timeless: as long as there are crypto networks and data sources, a Bloc Assistant can operate, adapting to whatever new exchanges or social platforms emerge in the future.
Incentive-driven and context-aware, Bloc Protocol aims to democratize advanced trading and asset management strategies, making them available in a decentralized manner to any early adopter or developer. Much like how Bitcoin allowed individuals to be their own banks, BLOC allows individuals to have their own autonomous crypto assistant working tirelessly on their behalf, under rules they control. The hope is that this protocol will foster a new generation of decentralized applications where automation and autonomy do not come at the price of trust or centralization, but instead reinforce the founding principles of the crypto ecosystem.